| Citations | 3245 |
| 2yr mean_citedness | 0.323 |
| h index | 21 |
| i10 index | 67 |
| ICV 2024 | 88.02 |
Search
Harnessing Artificial Intelligence to Strengthen Intrusion Detection in Modern Network System
Abstract : 302
PDF : 112
Pre-Service Teachers’ Perception of Online Teaching and Learning During the COVID – 19 Era
Abstract : 442
PDF : 230
XML : 95
Enhancing Cloud Security: Implementing Zero Trust Architectures in Multi-Cloud Environments
Abstract : 240
PDF : 157
Improved Privacy over Authentication of K-Nearest Neighbor Query on Spatial Network
Abstract : 56
PDF : 38
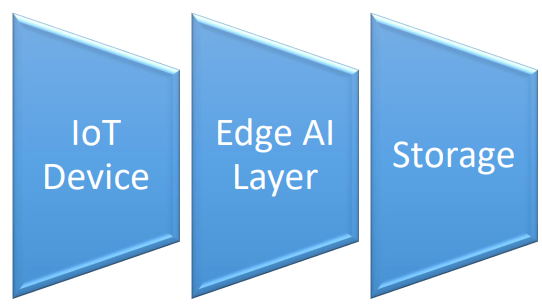
Optimizing Edge AI for Real-Time Data Processing in IoT Devices: Challenges and Solutions
Abstract : 651
PDF : 190
Remote execution of physical tasks by putting into contributionDOSN: Case of Money Transfer
Abstract : 203
PDF : 212
Fuzzy Logic Based Handover decision and Necessity Estimation Scheme for Heterogeneous Wireless Networks
Abstract : 44
PDF : 30
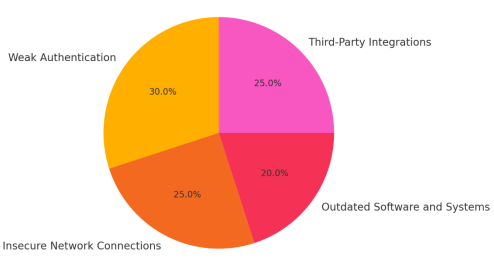
Social Engineering Attacks in US Healthcare: A Critical Analysis of Vulnerabilities and Mitigation Strategies
Abstract : 402
PDF : 319
Zero Trust Architecture and Business Risk Alignment: Comprehensive Governance Framework, Implementation Methodologies, and Future Security Trends for Enterprise Environments
Abstract : 172
PDF : 228
Comprehensive Cyber Risk Governance Frameworks and Implementation Methodologies for AI-Augmented Enterprises: Architectural Considerations, Standards Alignment, Case Studies, and Future Directions
Abstract : 173
PDF : 145