| Citations | 3245 |
| 2yr mean_citedness | 0.323 |
| h index | 21 |
| i10 index | 67 |
| ICV 2024 | 88.02 |
Search
Harnessing Artificial Intelligence to Strengthen Intrusion Detection in Modern Network System
Abstract : 259
PDF : 84
AI-Augmented Data Engineering Strategies for Real-Time Fraud Detection in Digital Ecosystems
Abstract : 180
PDF : 134
Designing Scalable Software Automation Frameworks for Cybersecurity Threat Detection and Response
Abstract : 488
PDF : 170
AI-Augmented Vulnerability Discovery through Static Code Pattern Clustering in Micro services
Abstract : 500
PDF : 141
National Predictive Analytics Framework for Preventing Healthcare Fraud and Abuse
Abstract : 193
PDF : 34
Machine Learning for Enhancing Mortgage Origination Processes: Streamlining and Improving Efficiency
Abstract : 247
PDF : 106
AI-Enabled Statistical Process Control for Semiconductor Manufacturing Quality Improvement
Abstract : 1169
PDF : 367
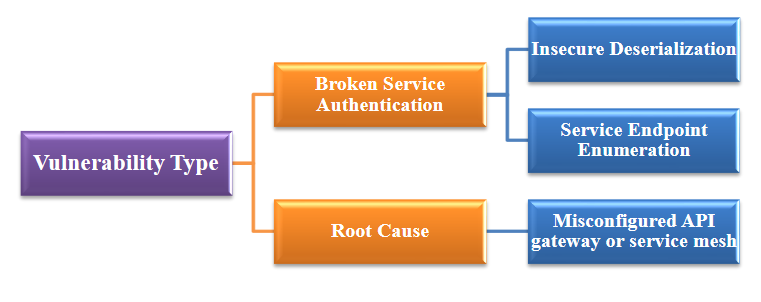
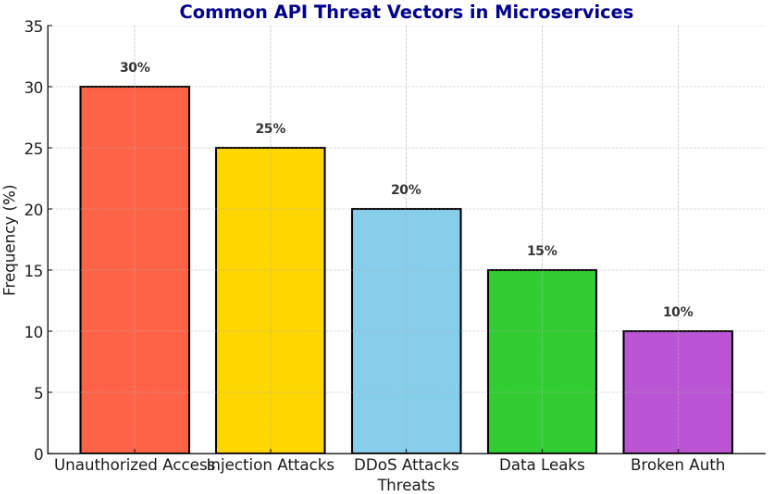
Dynamic Adaptive API Security Framework Using AI-Powered Blockchain Consensus for Microservices
Abstract : 156
PDF : 60
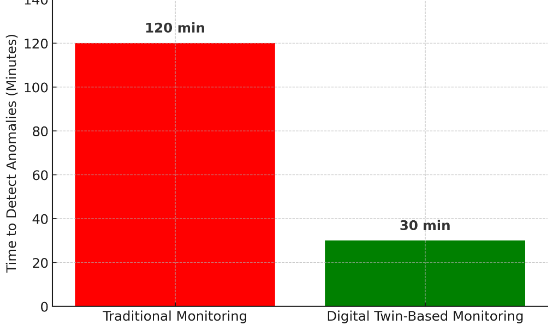
Digital Twins in IT: Enhancing System Monitoring and Predictive Maintenance
Abstract : 155
PDF : 113
Use of Artificial Intelligence in Medical Devices for Post-Market Surveillance
Abstract : 491
PDF : 335
Improving Distributed Cloud Data Engineering with AI-Powered Failure Prediction Systems
Abstract : 148
PDF : 83
Machine Learning-Powered Monitoring Systems for Improved Data Reliability in Cloud Environments
Abstract : 112
PDF : 77
Deep Learning Techniques for Adaptive Resource Allocation and Data Reliability in Cloud Ecosystems
Abstract : 115
PDF : 90
AIOps in cloud computing: Automation performance Monitoring with AI and New Relic
Abstract : 200
PDF : 73