| Citations | 3245 |
| 2yr mean_citedness | 0.323 |
| h index | 21 |
| i10 index | 67 |
| ICV 2024 | 88.02 |
Search
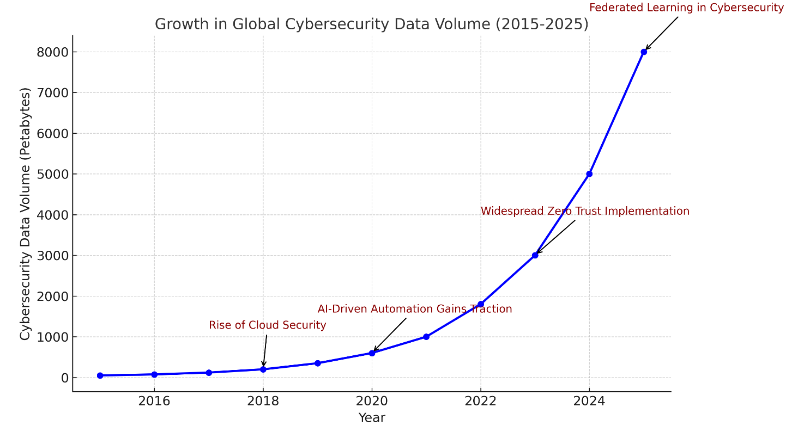
Designing Scalable Software Automation Frameworks for Cybersecurity Threat Detection and Response
Abstract : 498
PDF : 177
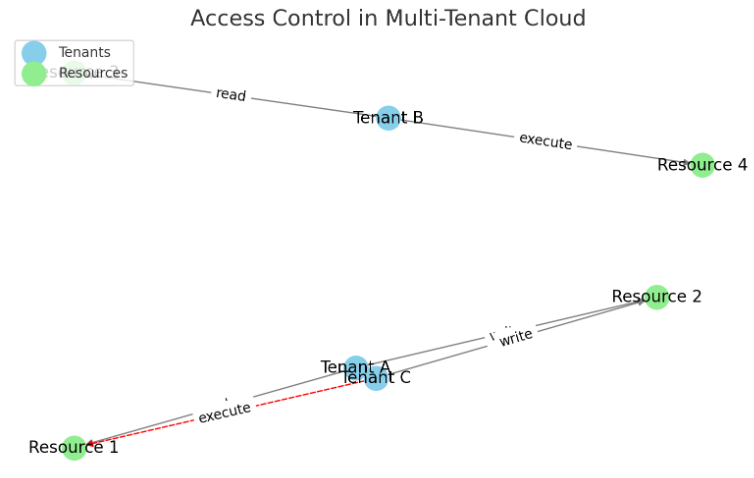
Enhancing Cloud Security: Implementing Zero Trust Architectures in Multi-Cloud Environments
Abstract : 234
PDF : 157
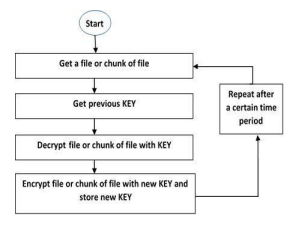
Secured Auto Encryption and Authentication Process for Cloud Computing Security
Abstract : 349
PDF : 164
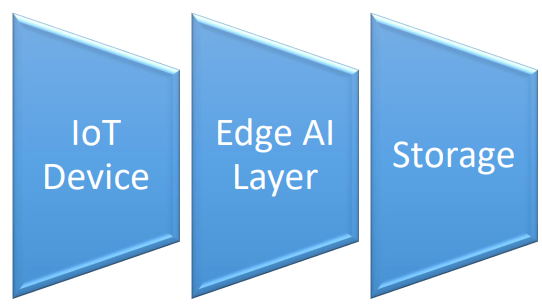
Optimizing Edge AI for Real-Time Data Processing in IoT Devices: Challenges and Solutions
Abstract : 629
PDF : 185
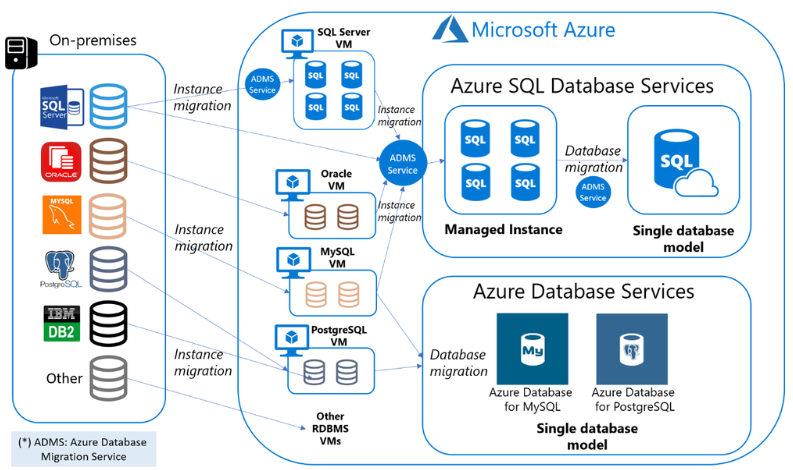
Optimizing Hybrid Cloud Database Architecture: Integrating SQL Server and MongoDB in Azure Environments
Abstract : 352
PDF : 120
Towards Computational Synergy: Present State-of-the-art of Mobile Cloud Computing
Abstract : 109
PDF : 81
A Secure Anti-Collusion Data Sharing Scheme for Dynamic Groups in the Cloud by using Identity based Encryption
Abstract : 214
PDF : 79
A Noval Approach of Enhancing Security in Cloud Using Diffie Hellman Algorithm
Abstract : 61
PDF : 36
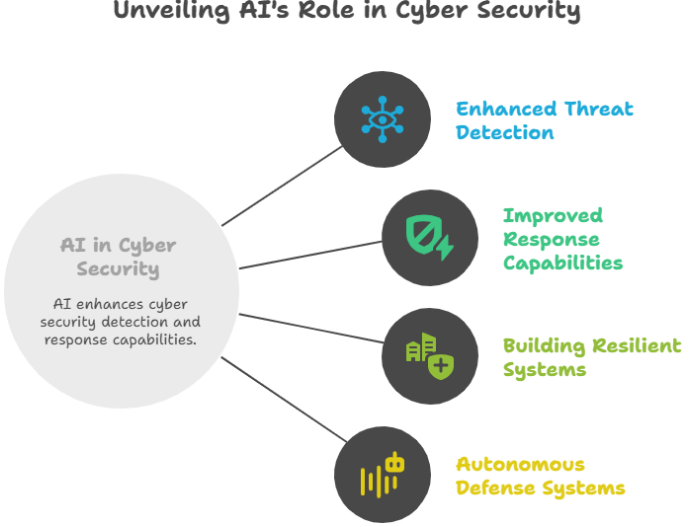
Harnessing Artificial Intelligence to Strengthen Intrusion Detection in Modern Network System
Abstract : 276
PDF : 94
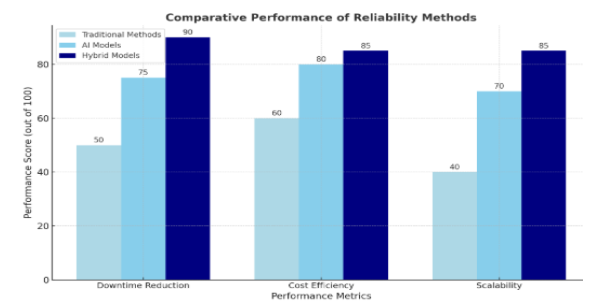
Hybrid Models for AI-Powered Automation In Cloud Data Reliability Engineering
Abstract : 190
PDF : 73
A Quantitative Assessment of the Impact of Automated Incident Response on Cloud Services Availability
Abstract : 307
PDF : 170
Enhancement in OTP generation process for cloud data security using Diffie-Hellman and HMAC - A Review
Abstract : 117
PDF : 94
Building Cognitive Data Lakes on Cloud: Integrating NLP and AI to Make Data Lakes Smart
Abstract : 232
PDF : 95
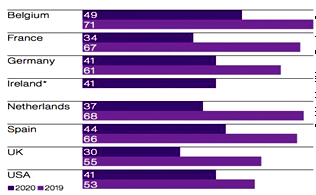
Data privacy in cloud computing: A comparative study of privacy preserving techniques
Abstract : 482
PDF : 356
Advanced Cybersecurity Strategies for Protecting Critical Infrastructure: Strengthening the Backbone of National Security
Abstract : 482
PDF : 154
SECURE DATA SHARING FOR DYNAMIC GROUPS IN THE CLOUD USING BROADCASTING ENCRYPTION TECHNIQUES
Abstract : 101
PDF : 98
Machine Learning-Powered Monitoring Systems for Improved Data Reliability in Cloud Environments
Abstract : 118
PDF : 80
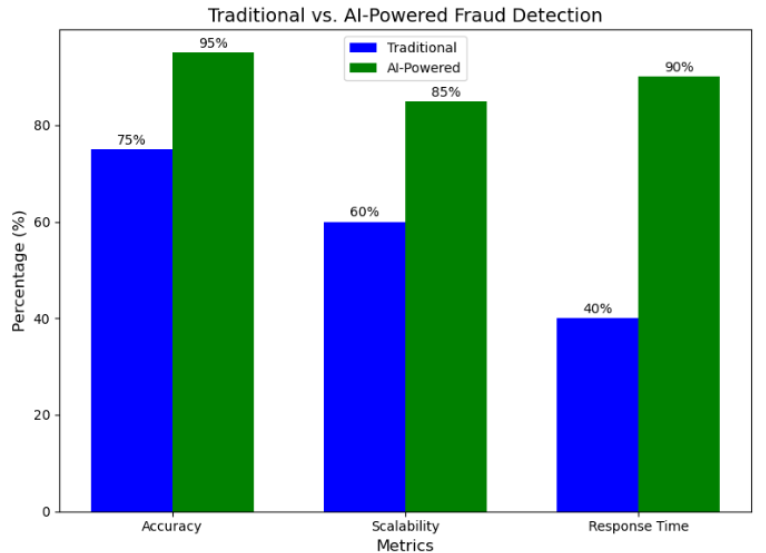
AI-Augmented Data Engineering Strategies for Real-Time Fraud Detection in Digital Ecosystems
Abstract : 191
PDF : 148