| Citations | 3245 |
| 2yr mean_citedness | 0.323 |
| h index | 21 |
| i10 index | 67 |
| ICV 2024 | 88.02 |
Search
1 - 18 of 18 items
DATA PRIVACY AND REGULATORY COMPLIANCE IN THE USA: A CALL FOR A CENTRALIZED REGULATORY FRAMEWORK
Abstract : 882
PDF : 189
Integrity and Confidentiality of Data Protection on Consumers' Privacy in Tanzania: A Case Study of TCRA
Abstract : 360
PDF : 266
Extensiveness of Children's Self-Protection Training Strategy By Parent-Teacher on Enhancing Curbing of Abuse in Public Primary Schools In Kinondoni Municipality, Tanzania
Abstract : 1591
PDF : 214
Data privacy in cloud computing: A comparative study of privacy preserving techniques
Abstract : 492
PDF : 386
Innovative Data Collection Methods for Advancing Coastal Management in Liberia
Abstract : 533
PDF : 201
Enhancing Cloud Security: Implementing Zero Trust Architectures in Multi-Cloud Environments
Abstract : 240
PDF : 157
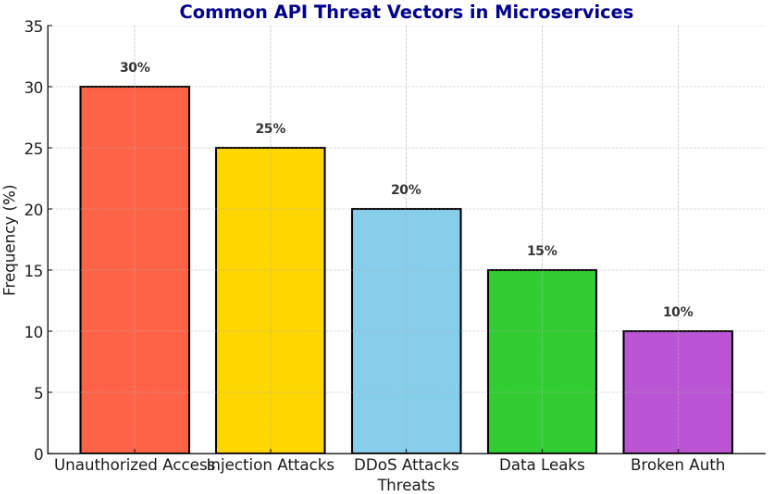
Dynamic Adaptive API Security Framework Using AI-Powered Blockchain Consensus for Microservices
Abstract : 167
PDF : 62
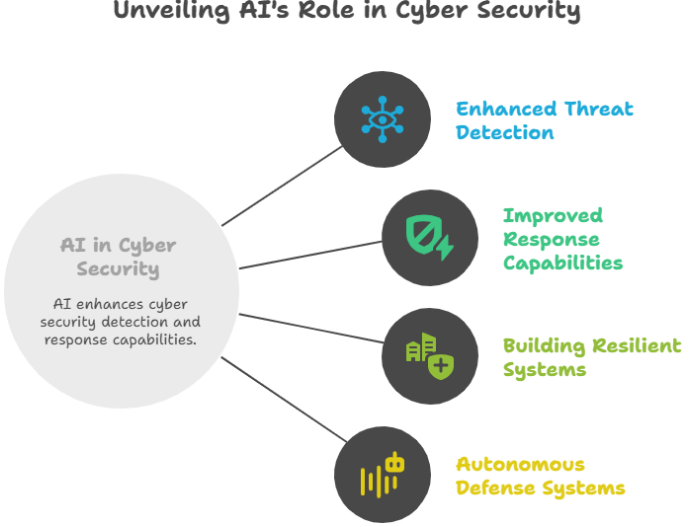
Harnessing Artificial Intelligence to Strengthen Intrusion Detection in Modern Network System
Abstract : 304
PDF : 117
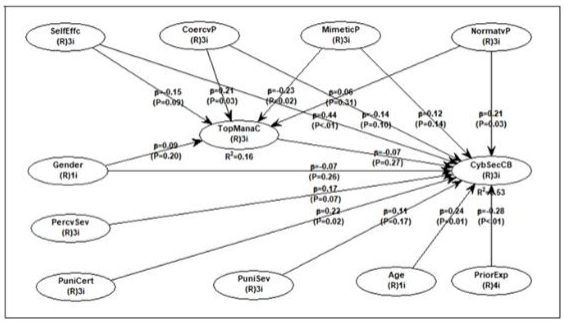
Factors That Influence Cybersecurity Compliance Behaviours by Bank Employees: A Case of Banks Operating In Kenya
Abstract : 1190
PDF : 189
Contribution of Counseling Assistance Services in the Support of the Students’ Acquisition of Life Skills among Public Secondary Schools in Moshi Municipality
Abstract : 437
PDF : 143
A Secure Anti-Collusion Data Sharing Scheme for Dynamic Groups in the Cloud by using Identity based Encryption
Abstract : 216
PDF : 81
Computer Security and Intrusion detection System-A Data Mining Based Approach
Abstract : 94
PDF : 67
1 - 18 of 18 items