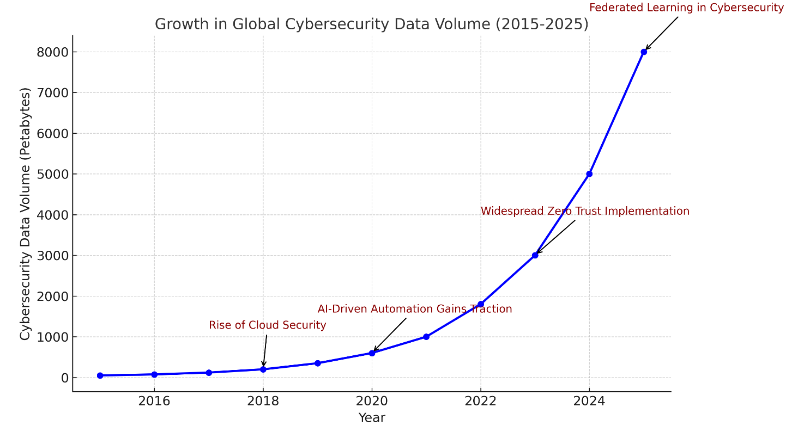
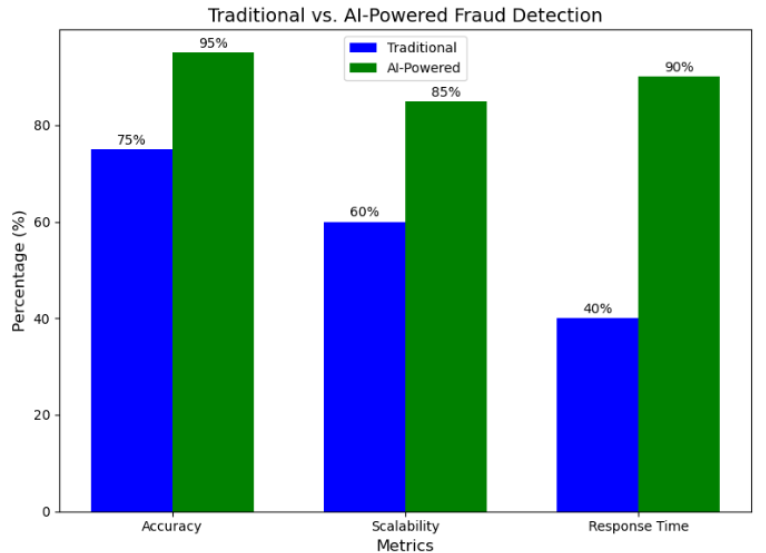
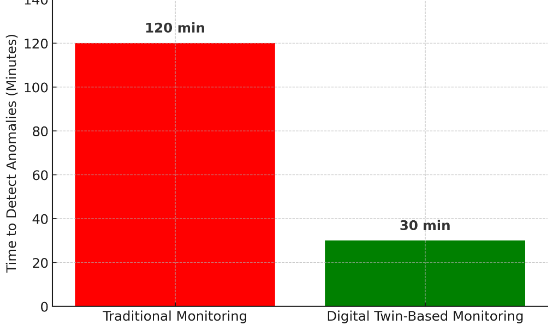
| Citations | 3245 |
| 2yr mean_citedness | 0.323 |
| h index | 21 |
| i10 index | 67 |
| ICV 2024 | 88.02 |
Search
1 - 15 of 15 items
Designing Scalable Software Automation Frameworks for Cybersecurity Threat Detection and Response
Abstract : 530
PDF : 191
AI-Augmented Data Engineering Strategies for Real-Time Fraud Detection in Digital Ecosystems
Abstract : 211
PDF : 172
Digital Twins in IT: Enhancing System Monitoring and Predictive Maintenance
Abstract : 162
PDF : 139
Revolutionizing Cybersecurity: Behavioral Analysis and Automated Incident Response through Predictive Analytics
Abstract : 200
PDF : 124
The Evolution of Security Operations Centers (SOCs): Shifting from Reactive to Proactive Cybersecurity Strategies
Abstract : 311
PDF : 127
Scalable Data Engineering Approaches For Ai-Driven Industrial Iot Applications
Abstract : 194
PDF : 108
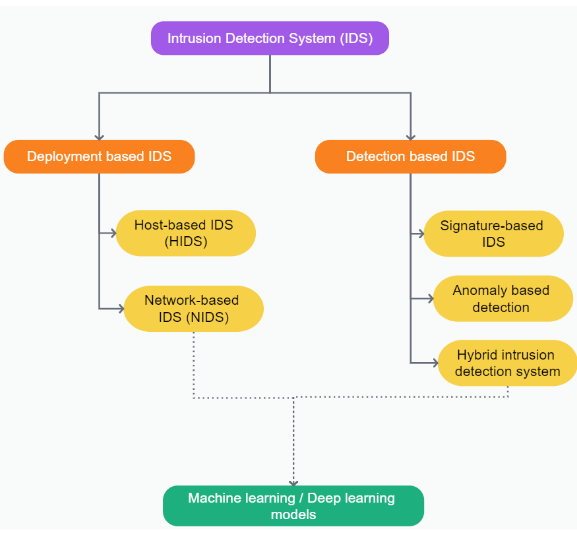
Harnessing Artificial Intelligence to Strengthen Intrusion Detection in Modern Network System
Abstract : 309
PDF : 119
1 - 15 of 15 items