| Citations | 3245 |
| 2yr mean_citedness | 0.323 |
| h index | 21 |
| i10 index | 67 |
| ICV 2024 | 88.02 |
Search
1 - 17 of 17 items
Harnessing Artificial Intelligence to Strengthen Intrusion Detection in Modern Network System
Abstract : 304
PDF : 117
Designing Scalable Software Automation Frameworks for Cybersecurity Threat Detection and Response
Abstract : 530
PDF : 184
Bridging Borders with AI: Enhancing Global Cybersecurity Through Intelligent Threat Detection
Abstract : 176
PDF : 88
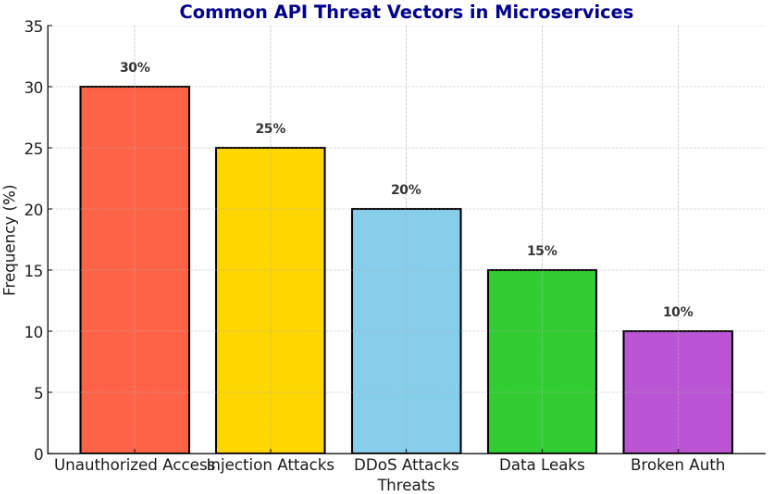
Dynamic Adaptive API Security Framework Using AI-Powered Blockchain Consensus for Microservices
Abstract : 167
PDF : 62
The Evolution of Ransomware: Tactics, Techniques, and Mitigation Strategies
Abstract : 1217
PDF : 524
Social Engineering Attacks in US Healthcare: A Critical Analysis of Vulnerabilities and Mitigation Strategies
Abstract : 402
PDF : 321
Emerging Threats: The Latest Cybersecurity Risks and the Role of Artificial Intelligence in Enhancing Cybersecurity Defenses
Abstract : 1306
PDF : 553
1 - 17 of 17 items