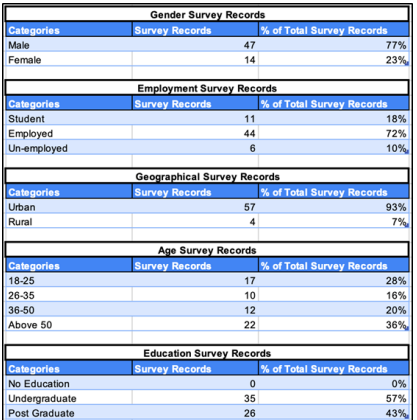
| Citations | 3245 |
| 2yr mean_citedness | 0.323 |
| h index | 21 |
| i10 index | 67 |
| ICV 2024 | 88.02 |
Search
An Empirical Study on Cybersecurity Awareness, Cybersecurity Concern, and Vulnerability to Cyber-attacks
Abstract : 489
PDF : 354
Emerging Threats: The Latest Cybersecurity Risks and the Role of Artificial Intelligence in Enhancing Cybersecurity Defenses
Abstract : 1275
PDF : 540
Designing Scalable Software Automation Frameworks for Cybersecurity Threat Detection and Response
Abstract : 520
PDF : 182
Bridging Borders with AI: Enhancing Global Cybersecurity Through Intelligent Threat Detection
Abstract : 165
PDF : 86
Improving resilience and efficiency in the energy sector: A perspective on cybersecurity and renewable energy storage.
Abstract : 574
PDF : 212
Advanced Cybersecurity Strategies for Protecting Critical Infrastructure: Strengthening the Backbone of National Security
Abstract : 485
PDF : 157
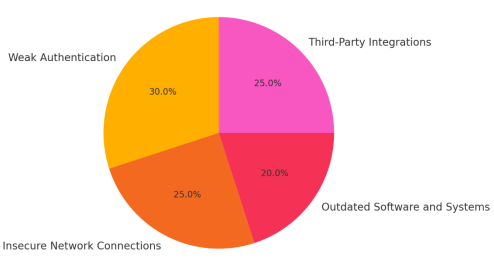
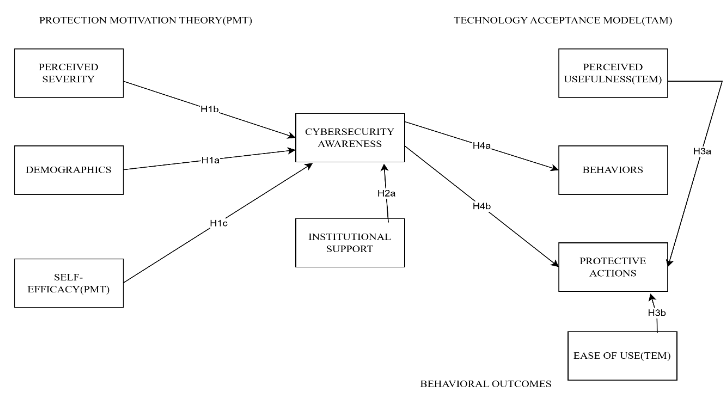
An Integrated PMT-TAM Approach to Cybersecurity Awareness: Evidence from Sierra Leone's Universities and Policy Lessons for Developing Nations
Abstract : 183
PDF : 145
Social Engineering Attacks in US Healthcare: A Critical Analysis of Vulnerabilities and Mitigation Strategies
Abstract : 390
PDF : 312
The Future of Electric Vehicles: Navigating the Intersection of AI, Cloud Technology, and Cybersecurity
Abstract : 433
PDF : 291
Revolutionizing Cybersecurity: Behavioral Analysis and Automated Incident Response through Predictive Analytics
Abstract : 199
PDF : 119
The Evolution of Security Operations Centers (SOCs): Shifting from Reactive to Proactive Cybersecurity Strategies
Abstract : 307
PDF : 127
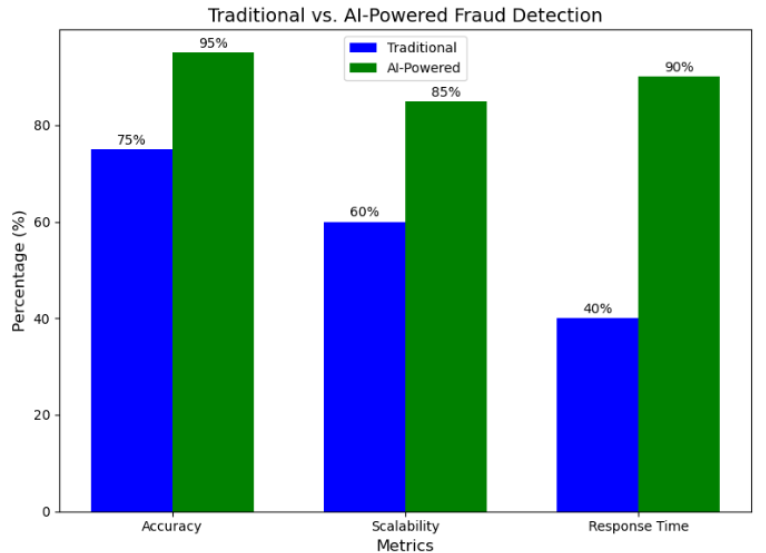
AI-Augmented Data Engineering Strategies for Real-Time Fraud Detection in Digital Ecosystems
Abstract : 197
PDF : 152
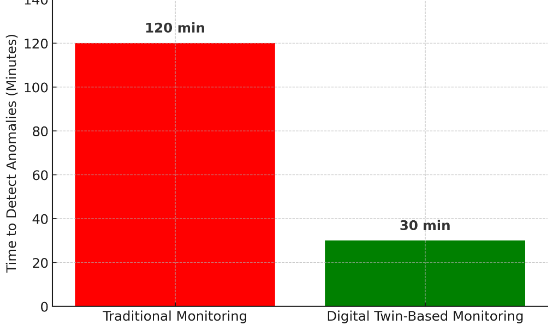
Digital Twins in IT: Enhancing System Monitoring and Predictive Maintenance
Abstract : 159
PDF : 132
The Evolution of Ransomware: Tactics, Techniques, and Mitigation Strategies
Abstract : 1193
PDF : 505