| Citations | 3245 |
| 2yr mean_citedness | 0.323 |
| h index | 21 |
| i10 index | 67 |
| ICV 2024 | 88.02 |
Search
DATA PRIVACY AND REGULATORY COMPLIANCE IN THE USA: A CALL FOR A CENTRALIZED REGULATORY FRAMEWORK
Abstract : 871
PDF : 188
Data privacy in cloud computing: A comparative study of privacy preserving techniques
Abstract : 486
PDF : 369
Integrity and Confidentiality of Data Protection on Consumers' Privacy in Tanzania: A Case Study of TCRA
Abstract : 358
PDF : 260
Efficient Customer Data Privacy Management in Hadoop Ecosystems: A Scalable Query Engine Approach
Abstract : 213
PDF : 85
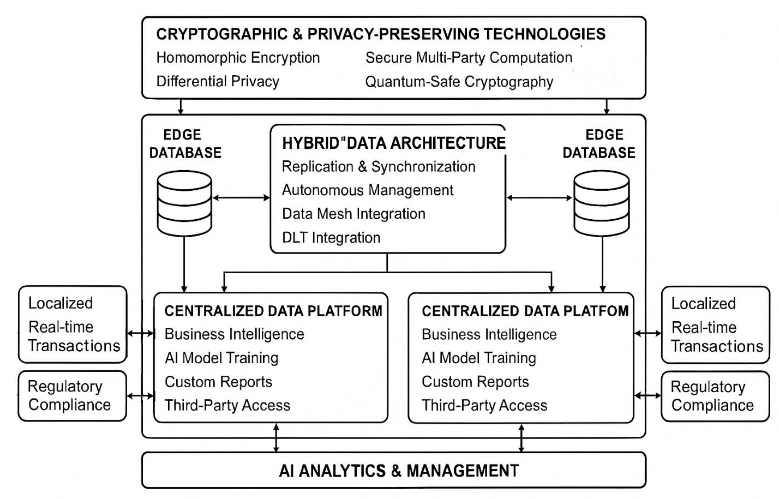
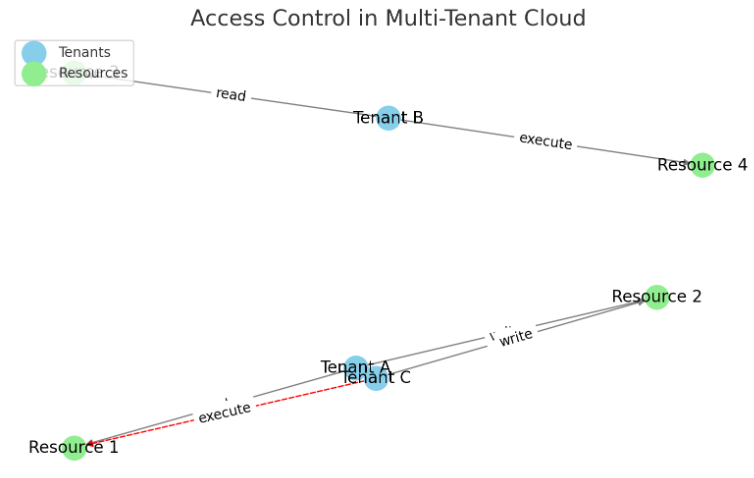
Advanced Database Strategies for Multi-Location Environments: Privacy, Security, and AI Integration
Abstract : 443
PDF : 129
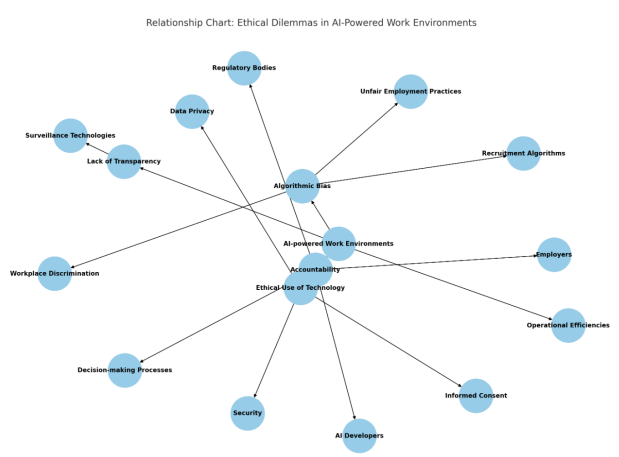
Ethical Considerations in AI-Powered Work Environments: A Literature Review and Theoretical Framework for Ensuring Human Dignity and Fairness
Abstract : 2029
PDF : 828
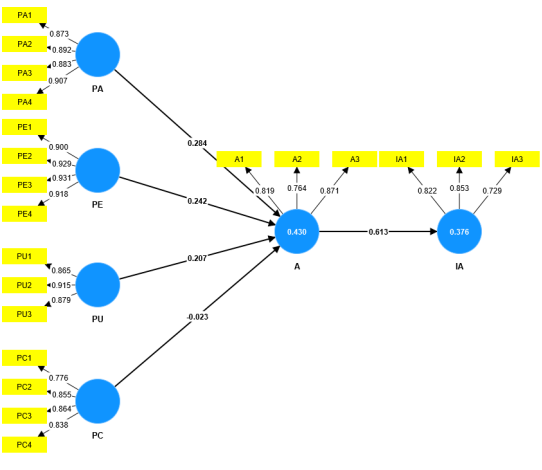
Customers Adaptation of E-banking services; extending TAM through Anthpmorphism in Saudi Arabia
Abstract : 414
PDF : 202
Fuzzy Based Implementation of Multi - Keyword Ranked Search over Encrypted Cloud Data in Secure Cloud Environment
Abstract : 173
PDF : 91
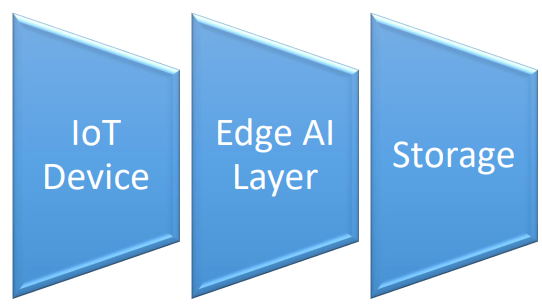
Optimizing Edge AI for Real-Time Data Processing in IoT Devices: Challenges and Solutions
Abstract : 640
PDF : 187
Architecting Cloud Database Solutions with Embedded AI for Real-Time Analytics
Abstract : 589
PDF : 107
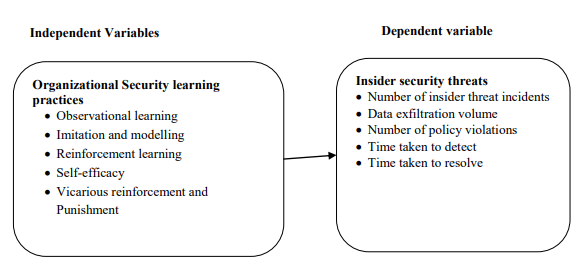
Influence of Organizational Security Learning Practices on Insider Security Threats in SoCs in Kenya
Abstract : 343
PDF : 122