| Citations | 3245 |
| 2yr mean_citedness | 0.323 |
| h index | 21 |
| i10 index | 67 |
| ICV 2024 | 88.02 |
Search
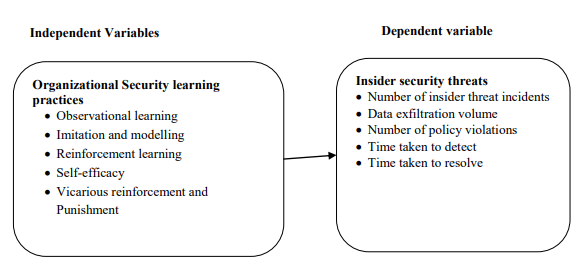
Influence of Organizational Security Learning Practices on Insider Security Threats in SoCs in Kenya
Abstract : 345
PDF : 124
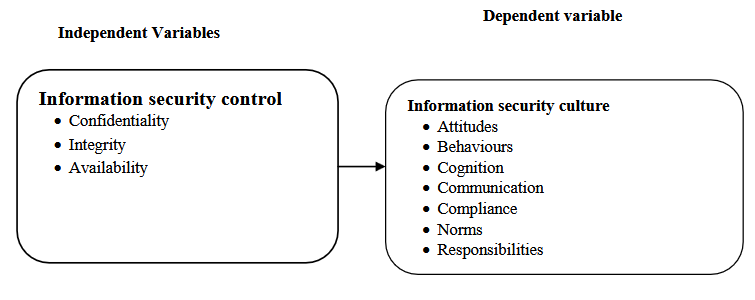
Factors Influencing Information Security Culture in Organizations Dealing With Economic Crime in Kenya
Abstract : 430
PDF : 185
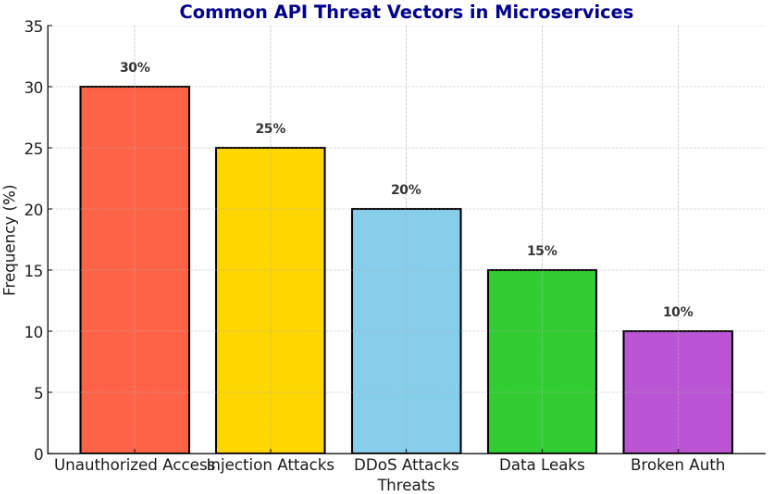
Dynamic Adaptive API Security Framework Using AI-Powered Blockchain Consensus for Microservices
Abstract : 167
PDF : 62
Designing Scalable Software Automation Frameworks for Cybersecurity Threat Detection and Response
Abstract : 530
PDF : 184
A Review of The Literature on An Examination of The Effects of Cyber Security in Improved Public Sector Institution Performance in Jordan
Abstract : 182
PDF : 100
Reflecting on the Impacts of the 2013 coup in Central Africa Republic on Economic Security
Abstract : 144
PDF : 162
From Terror to Titans: The Return of Nuclear Great Power Politics and the Decline of the Global War on Terrorism
Abstract : 165
PDF : 68
Factors That Influence the Uptake of an M-Pesa Security System among Mpesa Agents In Nairobi County
Abstract : 282
PDF : 117
PDF : 279
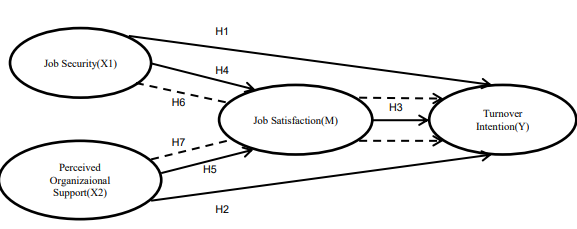
Understanding Turnover Intention: Exploring the Influence of Job Security, Perceived Organizational Support, and Job Satisfaction as a Mediator
Abstract : 919
PDF : 411
Harnessing Artificial Intelligence to Strengthen Intrusion Detection in Modern Network System
Abstract : 304
PDF : 117
Factors That Influence Cybersecurity Compliance Behaviours by Bank Employees: A Case of Banks Operating In Kenya
Abstract : 1190
PDF : 189
Leveraging Artificial Intelligence to Automate and Enhance Security Operations: Balancing Efficiency and Human Oversight
Abstract : 318
PDF : 128
Secured Auto Encryption and Authentication Process for Cloud Computing Security
Abstract : 350
PDF : 166
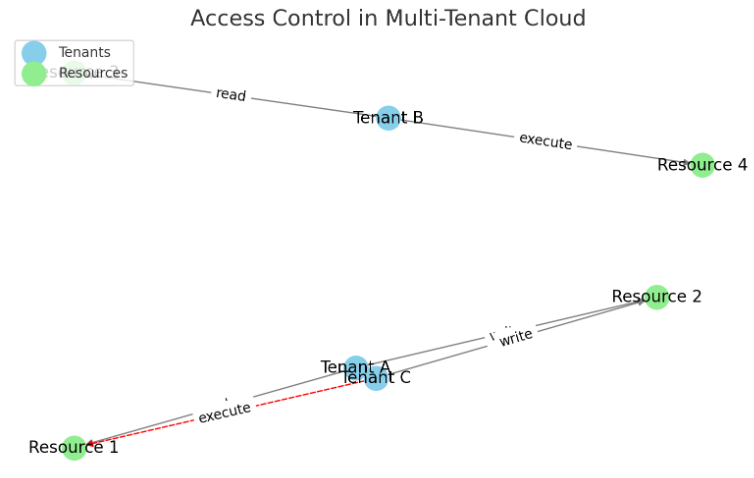
Enhancing Cloud Security: Implementing Zero Trust Architectures in Multi-Cloud Environments
Abstract : 240
PDF : 157
The Opposite of War is Not Peace: The Complex Realities of 21st Century Conflict
Abstract : 336
PDF : 123