| Citations | 3245 |
| 2yr mean_citedness | 0.323 |
| h index | 21 |
| i10 index | 67 |
| ICV 2024 | 88.02 |
Search
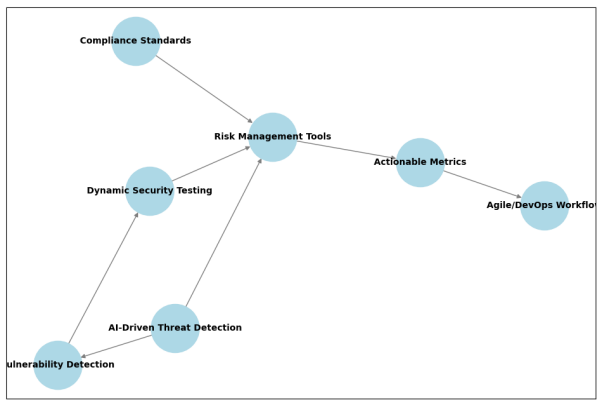
Dynamic Adaptive API Security Framework Using AI-Powered Blockchain Consensus for Microservices
Abstract : 159
PDF : 61
Factors Influencing Information Security Culture in Organizations Dealing With Economic Crime in Kenya
Abstract : 415
PDF : 177
Designing Scalable Software Automation Frameworks for Cybersecurity Threat Detection and Response
Abstract : 493
PDF : 175
The Legal Conundrum Of Non-Interest Banking. A Case Study Of Islamic Bank In Nigeria.
Abstract : 352
PDF : 96
XML : 80
Factors That Influence the Uptake of an M-Pesa Security System among Mpesa Agents In Nairobi County
Abstract : 260
PDF : 108
PDF : 213
The Opposite of War is Not Peace: The Complex Realities of 21st Century Conflict
Abstract : 310
PDF : 87
DATA PRIVACY AND REGULATORY COMPLIANCE IN THE USA: A CALL FOR A CENTRALIZED REGULATORY FRAMEWORK
Abstract : 829
PDF : 188
AI-Augmented Vulnerability Discovery through Static Code Pattern Clustering in Micro services
Abstract : 534
PDF : 143
Zero Trust Architecture and Business Risk Alignment: Comprehensive Governance Framework, Implementation Methodologies, and Future Security Trends for Enterprise Environments
Abstract : 160
PDF : 222
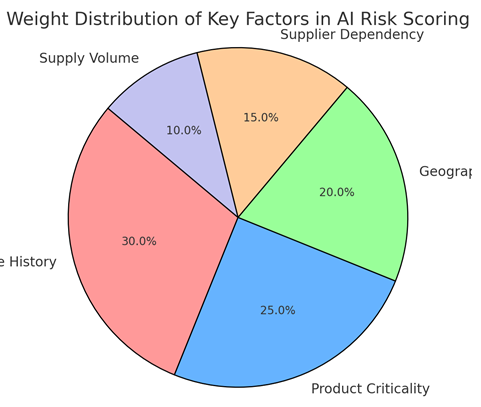
Transforming Supplier Audits with AI: A Risk-Based Approach in Medical Devices
Abstract : 527
PDF : 711
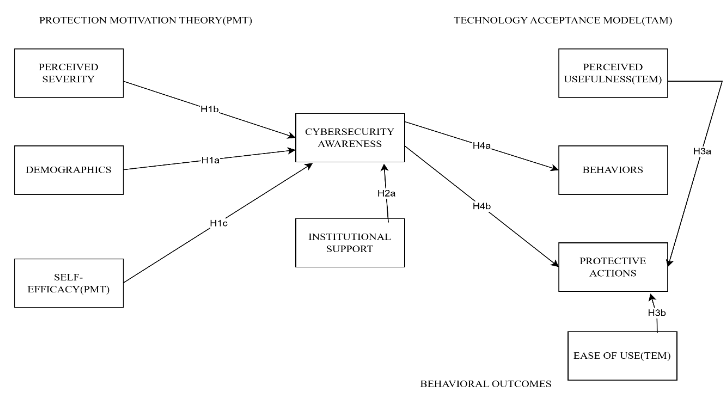
An Integrated PMT-TAM Approach to Cybersecurity Awareness: Evidence from Sierra Leone's Universities and Policy Lessons for Developing Nations
Abstract : 172
PDF : 114
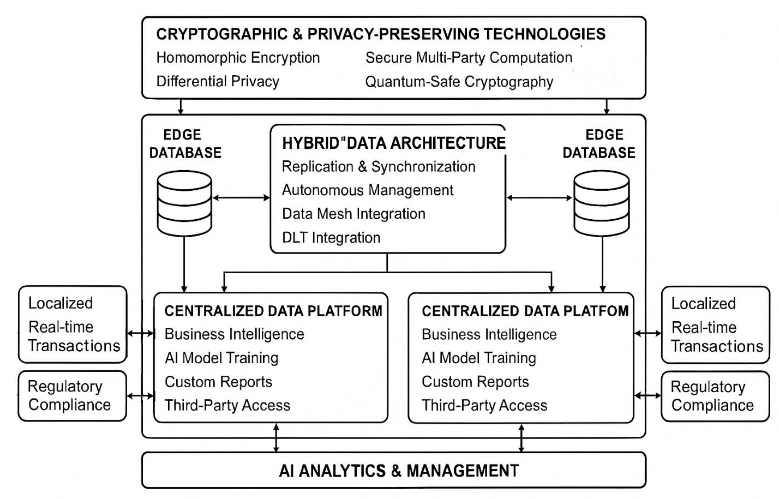
Advanced Database Strategies for Multi-Location Environments: Privacy, Security, and AI Integration
Abstract : 438
PDF : 126
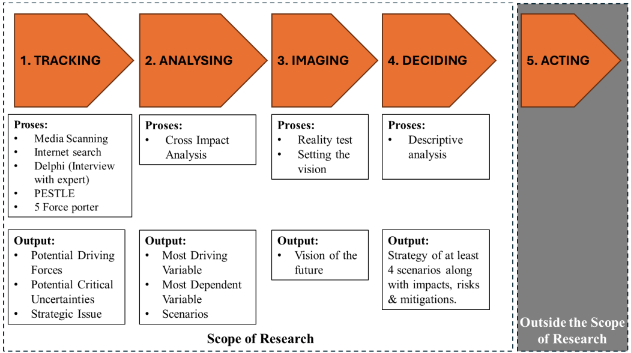
Scenario Planning Analysis of BPJS Kesehatan in Facing the Deficit of Social Security Fund for Health
Abstract : 393
PDF : 159
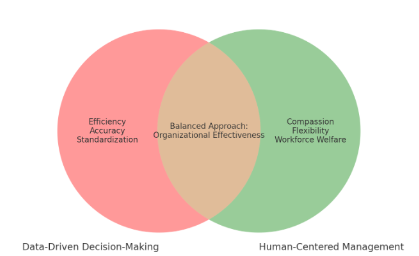
Bridging The Gap Between Data-Driven Decision Making and Human-Centric Management in Organisations
Abstract : 185
PDF : 146