| Citations | 3245 |
| 2yr mean_citedness | 0.323 |
| h index | 21 |
| i10 index | 67 |
| ICV 2024 | 88.02 |
Search
Identity and Image of A Private University After Incorporation Process: Students' Perception
Abstract : 504
PDF : 70
Postcolonial Identity Crisis in the Mimic Men a Novel by V.S.Naipaul
Abstract : 481
PDF : 159
XML : 81
L’ÉCRITURE COMME FORME D’IDENTITE CULTURELLE DANS LA LITTÉRATURE FRANCOPHONE À TRAVERS LE BAC DE CABRI MORT DE MAHAMADOU KONATÉ
Abstract : 442
PDF : 227
Nativization of Fear and Anxiety as Identity in Selected Fiction of East African Asians
Abstract : 163
PDF : 131
A study of personality factors (Openness and Conscientiousness) and perceived level of career success in married individuals.
Abstract : 72
PDF : 109
Multicultural Education as a Unifying Force for Values of Unity, Cohesion and National Identity in the Global Era in Indonesia
Abstract : 668
PDF : 79
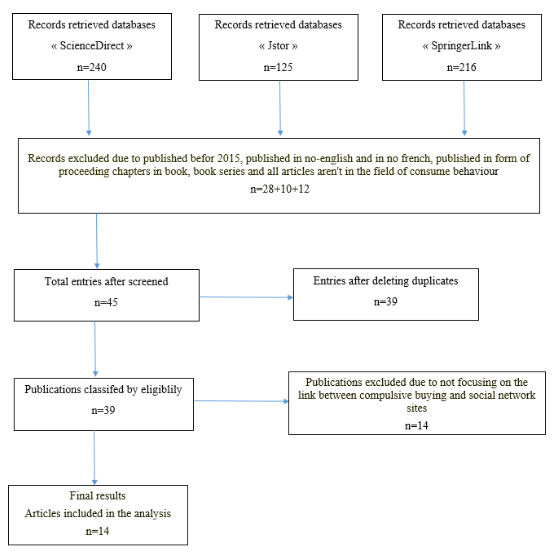
Use of social network sites and compulsive buying behavior: Litterature review using PRISMA
Abstract : 392
PDF : 128
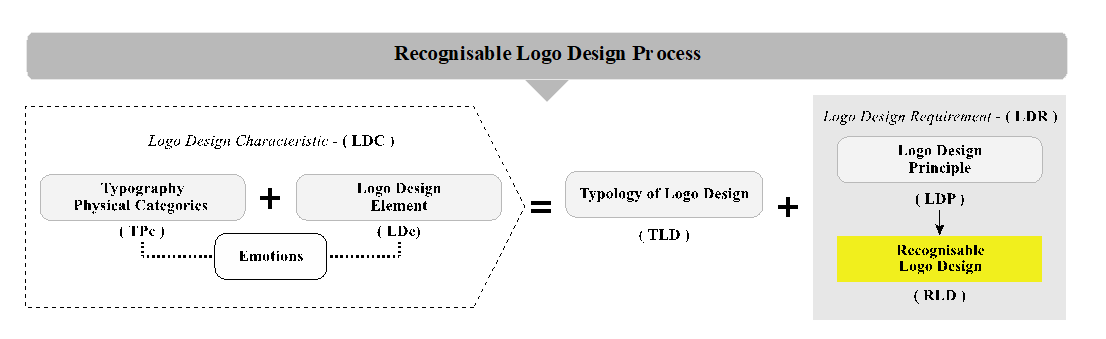
Development of the Recognisable Logo Design Guideline for Startup Brands
Abstract : 203
PDF : 93
XML : 71
Use of Stream of Consciousness in Brick Lane: A Psychoanalytical Approach to Study Nazneen’s Evolution
Abstract : 283
PDF : 311
A Secure Anti-Collusion Data Sharing Scheme for Dynamic Groups in the Cloud by using Identity based Encryption
Abstract : 109
PDF : 50
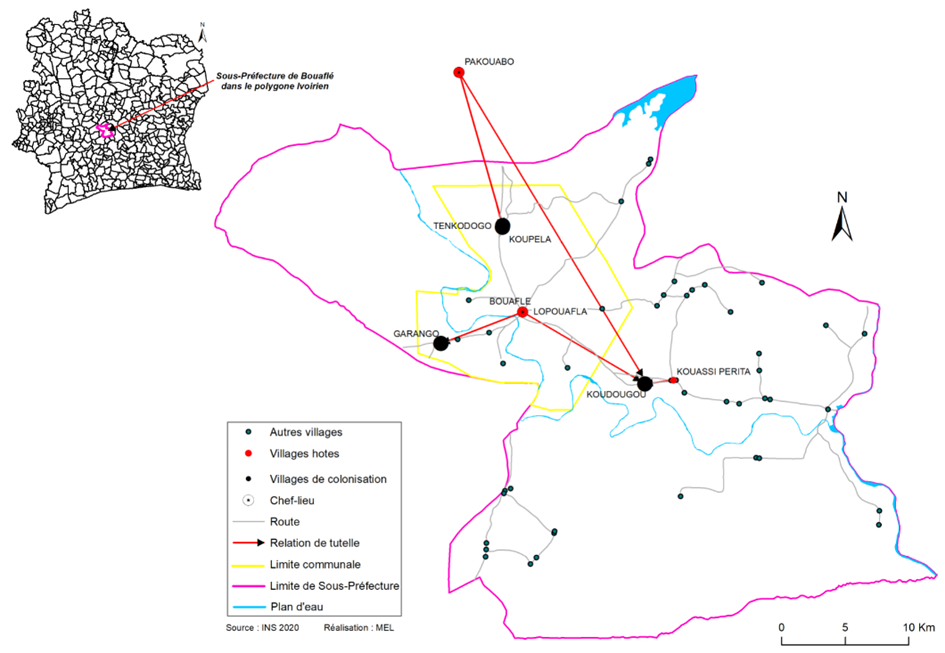
Reconstructing the origin among the descendants of naturalized voltaic immigrants Ivorians in Bouaflé Reconstruire l’origine chez les descendants d’immigrés voltaïques naturalisés Ivoiriens à Bouaflé
Abstract : 94
PDF : 98
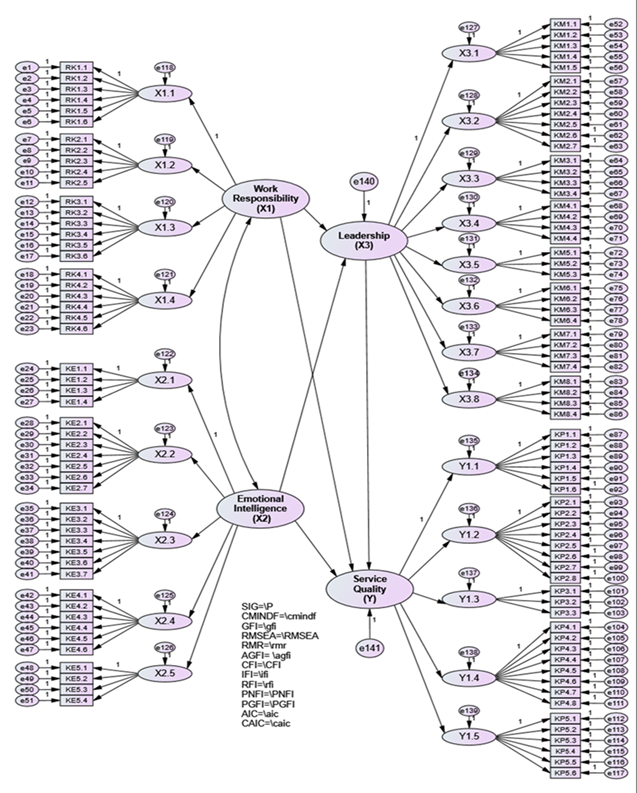
the The Effect of Job Responsibility, Emotional Intelligence, and Leadership on the Service Quality of Expert Staff for the People’s Representative Council of Indonesia
Abstract : 214
PDF : 93
##plugins.generic.jatsParser.publication.galley.pdf.label## : 46
XML : 69
Machine Learning for Enhancing Mortgage Origination Processes: Streamlining and Improving Efficiency
Abstract : 232
PDF : 98
Blockchain technology impact HR hiring and off-boarding practices in the Telco sector in Hong Kong
Abstract : 180
PDF : 218
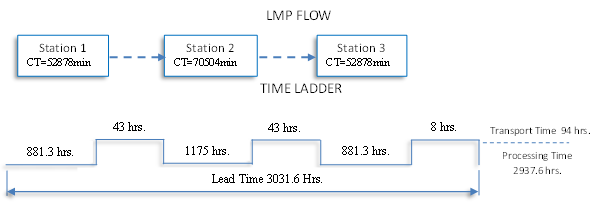
Looking for Employees Efficiency? Change the System through Value Stream Mapping
Abstract : 104
PDF : 78
Research for the Investigation of Consumer Attitudes towards Online Shopping in Niğde Province
Abstract : 110
PDF : 95
XML : 55
The Effect of Personality, Organizational Climate and Job Satisfaction on Teachers Organizational Citizenship Behavior at Public Vocational High School in DKI Jakarta Province
Abstract : 354
PDF : 125
XML : 61
Revitalizing Cooperative Human Resources: An Education and Perspective Analysis, Study at Medan Municipal City; Indonesia
Abstract : 329
PDF : 102
XML : 57
The Impact of the digitalization and the policy changes on the Savings Instruments (Saving Certificates) in Bangladesh: a response from the investors.
Abstract : 139
PDF : 173